Get started
Authentication
To use the EnterpriseEngage Deployments API, you need to authenticate with an access token:
- For user-service interactions, copy your user access token directly from a given application in Guidewire Home.
- For service-to-service interactions, use your client credentials to get a token with specific scopes.
Get a user access token
To authenticate with a user access token, you must be in the user group managed by Guidewire Hub. For details, see Access Cloud Platform apps and services.
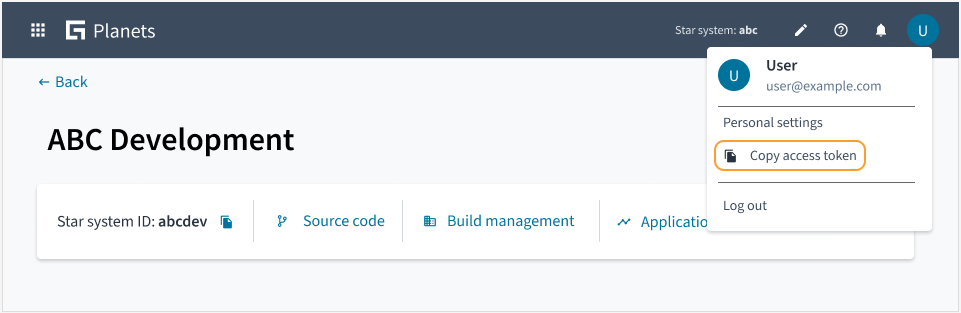
You can get an access token directly from Guidewire Home:
-
Log in to Guidewire Home.
In Guidewire Home, from
Apps, select Planets or select it from your pinned apps.
-
Select your profile.
-
Select
Copy access token.
This action copies an access token to your clipboard.
Get an access token with supported scopes
The EnterpriseEngage Deployments API supports the following scopes:
| Scope | Description |
|---|---|
gcc.digital.builds.read | Get a list of builds for a planet. |
gcc.digital.deployments.create | Deploy applications. |
gcc.digital.deployments.delete | Undeploy applications. |
gcc.digital.deployments.read | Get a list of application instances for particular parameters. Get details of an instance of an EnterpriseEngage application. Get a list of activities performed on a planet. Get details of an activity and tasks related to it. |
To get an access token with scopes, you must authenticate with Guidewire Hub using your client ID and client secret. Send the following POST request:
curl -s --location --request POST $GWHUB_URL \
--data-urlencode "grant_type=client_credentials" \
--data-urlencode "scope=tenant.{tenantId} project.{projectId} $SCOPES" \
--data-urlencode "client_id=$GWHUB_CLIENT_ID" \
--data-urlencode "client_secret=$GWHUB_CLIENT_SECRET" | jq -r '.access_token'
Where:
-
$GWHUB_URLdepends on your region. Use one of the following:Region URL AMER https://guidewire-hub.okta.com/oauth2/aus11vix3uKEpIfSI357/v1/tokenCANADA https://guidewire-hub.okta.com/oauth2/aus11vix3uKEpIfSI357/v1/tokenEMEA https://guidewire-hub-eu.okta.com/oauth2/ausc2q01c40dNZII0416/v1/tokenSWITZERLAND https://guidewire-hub-eu.okta.com/oauth2/ausc2q01c40dNZII0416/v1/tokenAPAC https://guidewire-hub-apac.okta.com/oauth2/ausbg05gfcTZQ7bpH3l6/v1/tokenJAPAN https://guidewire-hub-apac.okta.com/oauth2/ausbg05gfcTZQ7bpH3l6/v1/token -
$SCOPESis a list with at least one supported scope, separated by white spaces.Example:
gcc.digital.builds.read gcc.digital.deployments.create.
The response contains a JSON object with the requested access token:
{
"token_type": "Bearer",
"expires_in": 3600,
"access_token": "xxxxxxxx",
"scope": "scope=gcc.digital.builds.read gcc.digital.deployments.create tenant.{tenantId} project.{projectId}"
}
Make an authorized call
To authorize the API requests, add the obtained access token to an Authorization header:
Authorization: Bearer {access_token}
For example:
curl -s --location --request GET "$EE_DEPLOYMENTS_URL" \
-H "Accept: application/json" \
-H "Content-Type: application/json" \
-H "Authorization: Bearer $ACCESS_TOKEN"
Base URLs
Depending on your region, use one of the following base URLs:
| Region | URL |
|---|---|
| AMER | https://ee-deployer.api.omega2-andromeda.guidewire.net/backend/digitaldeployer/ |
| CANADA | https://ee-deployer.api.omega2-butterfly.guidewire.net/backend/digitaldeployer/ |
| EMEA | https://ee-deployer.api.omega2-cartwheel.guidewire.net/backend/digitaldeployer/ |
| SWITZERLAND | https://ee-deployer.api.omega2-whirlpool.guidewire.net/backend/digitaldeployer/ |
| APAC | https://ee-deployer.api.omega2-circinus.guidewire.net/backend/digitaldeployer/ |
| JAPAN | https://ee-deployer.api.omega2-milkyway.guidewire.net/backend/digitaldeployer/ |
When the documentation refers to {baseUrl}, replace it with the correct URL for your region.