Authentication concepts
Jutro provides two authentication clients - a native Okta client and a generic OpenID Connect (OIDC) authentication client.
Okta is an Identity Provider (IdP) that follows the OpenID Connect (OIDC) standard. The native Okta client is designed specifically for Okta. You can use the generic OIDC client to authenticate with any other IdP that supports the OIDC standard.
The client supports authentication by default, but not authorization. However, you are free to implement authorization in your application. See the authorization section for more details.
OIDC concepts
OpenID Connect (OIDC) allows you to enable authentication for your application. It works in connection with an Identity Provider (IdP) that is responsible for authentication and authorization. The IdP is usually a third-party service that you need to configure and manage.
Your application redirects the user to the IdP login page. After the user authenticates successfully, the IdP redirects them back to your application with an authorization code. Your application exchanges this code for an access token and a refresh token. The access token allows access to protected resources, while the refresh token is used to renew the access token when it expires.
In OIDC, this process is called the Authorization Code Flow. You can learn more about OIDC and the Authorization Code Flow in the following articles:
Please note that in @jutro/auth, Proof Key for Code Exchange (PKCE) is always enabled. You can learn more about PKCE in the following places:
The @jutro/auth package provides two clients for use with OIDC IdPs - an Okta client for use with the Okta IdP and a generic client for use with any OIDC complaint IdP. These clients provide handy components, hooks, and functions which can speed up your implementation of authentication.
Authorization
Jutro itself does not perform user authorization. User authorization must be implemented through the Cloud API authorization configuration mechanism.
When a user is prompted to log in, they are redirected to Guidewire Identity Federation Hub (Guidewire Hub) for authentication. If successful, Guidewire Hub returns an encoded access token that is included in future requests to the Cloud API. The Cloud API uses this token to determine if the user is authorized to make the requests it receives.
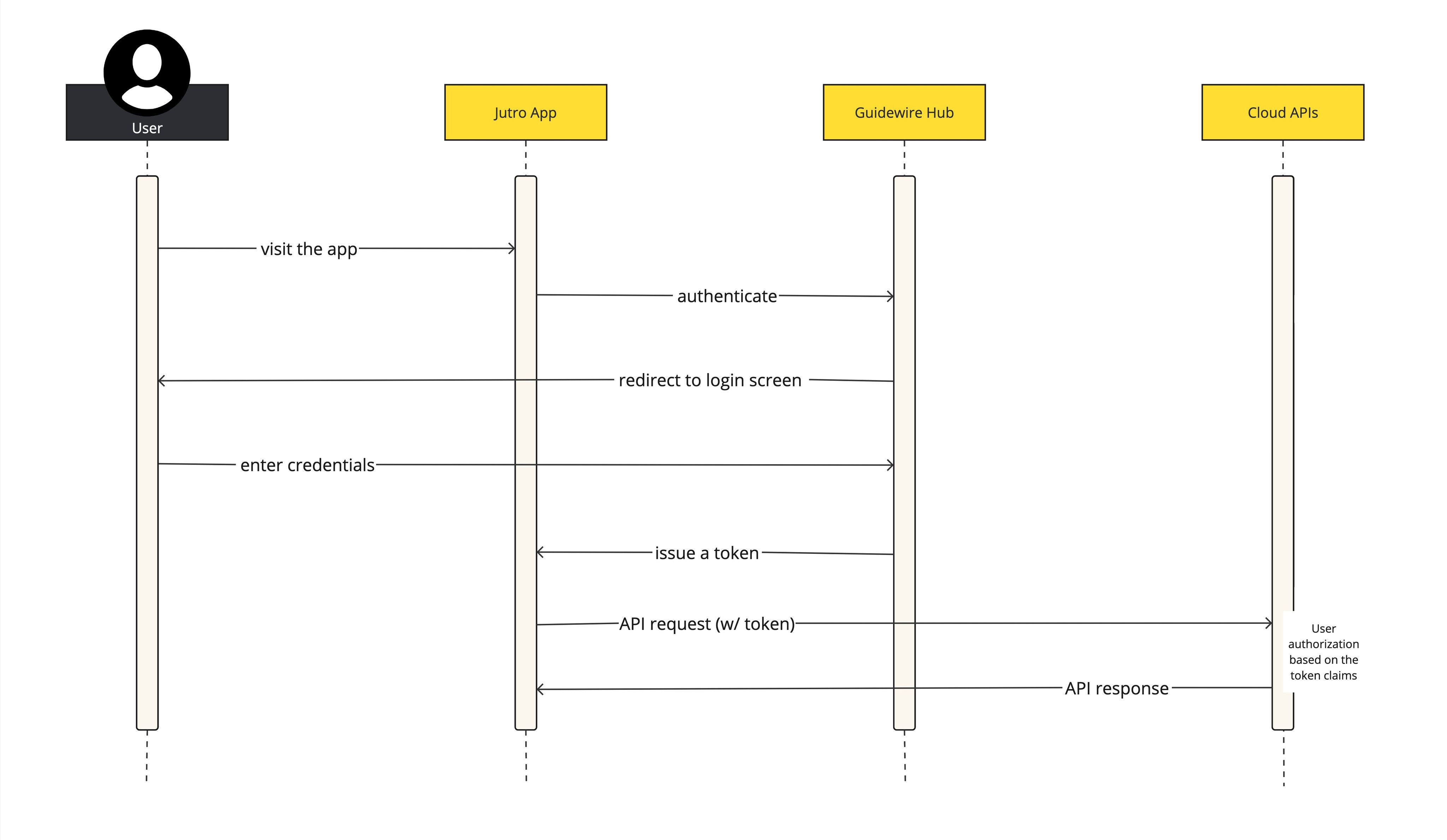
For more information, see Configuring InsuranceSuite authorization groups in Jutro Web Apps and the authorization documentation for your InsuranceSuite App: